- More than 30 modules to automatize administration and post exploitation tasks:
- Execute commands and browse remote filesystem, even with PHP security restriction
- Audit common server misconfigurations
- Run SQL console pivoting on target machine
- Proxy your HTTP traffic through target
- Mount target filesystem to local mount point
- Simple file transfer from and to target
- Spawn reverse and direct TCP shells
- Bruteforce SQL accounts through target system
- Run port scans from target machine
- And so on..
- Backdoor communications are hidden in HTTP Cookies
- Communications are obfuscated to bypass NIDS signature detection
- Backdoor polymorphic PHP code is obfuscated to avoid HIDS AV detection
Saturday, April 20, 2013
Weevely : Stealth PHP web shell with telnet style console
BlindElephant – Web Application Fingerprinting
The BlindElephant Web Application Finger-printer attempts to discover the version of a (known) web application by comparing static files at known locations against precomputed hashes for versions of those files in all all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatically.
BlindElephant works via a new trendy technique of fetching static elements of the web app such as .js, .css, and other core files then running a check sum to compare sizes of those files from released versions.
BlindElephant is available via SVN here
WebSploit Framework 2.0.3 with Wifi Jammer
WebSploit Is An Open Source Project For Scan And Analysis Remote System From Vulnerability.
[>]Social Engineering Works
[>]Scan,Crawler & Analysis Web
[>]Automatic Exploiter
[>]Support Network Attacks
----
[+]Autopwn - Used From Metasploit For Scan and Exploit Target Service
[+]wmap - Scan,Crawler Target Used From Metasploit wmap plugin
[+]format infector - inject reverse & bind payload into file format
[+]phpmyadmin Scanner
[+]LFI Bypasser
[+]Apache Users Scanner
[+]Dir Bruter
[+]admin finder
[+]MLITM Attack - Man Left In The Middle, XSS Phishing Attacks
[+]MITM - Man In The Middle Attack
[+]Java Applet Attack
[+]MFOD Attack Vector
[+]USB Infection Attack
[+]ARP Dos Attack
[+]Web Killer Attack
[+]Fake Update Attack
[+]Fake Access point Attack
Download WebSploit Framework 2.0.3
Nessus 5.0.2 vulnerability scanner updates
Nessus is the world’s most widely-deployed vulnerability and configuration assessment product updated to version 5.0.2 .Nessus 5 features high-speed discovery, configuration auditing, asset profiling, sensitive data discovery, patch management integration, and vulnerability analysis of your security posture with features that enhance usability, effectiveness, efficiency, and communication with all parts of your organization.
Nessus 5.0.2 change logs:
- UTF8 encoding problems would sometimes cause the generation of reports to fail
- Fixed a case where generating some compliance checks reports would cause the scanner to hang, using 100% of the CPU
- Resolved a resource leak issue occurring when a large number of different users are connected at the same time .
- Network congestion errors are now detected more conservatively
- Upgraded libxml2, libxslt, openssl to their newest versions
- Some nessusd.rules directives were not honored by the port scanners
- Solaris 10 build
Wifi Honey - Creates fake APs using all encryption
This is a script, attack can use to creates fake APs using all encryption and monitors with Airodump. It automate the setup process, it creates five monitor mode interfaces, four are used as APs and the fifth is used for airdump-ng. To make things easier, rather than having five windows all this is done in a screen session which allows you to switch between screens to see what is going on. All sessions are labelled so you know which is which.
Installing wifi honey
chmod a+x wifi_honey.sh
./wifi_honey.sh fake_wpa_net
./wifi_honey.sh fake_wpa_net 1 waln1
Download Wifi Honey
Biggest password cracking wordlist with millions of words
One of the biggest and very comprehensive collection of 1,493,677,782 word for Password cracking list released for download. The wordlists are intended primarily for use with password crackers such as hashcat, John the Ripper and with password recovery utilities.
Defuse Security have released the wordlist of 4.2 GiB (compressed) or 15 GiB (uncompressed) used by their Crackstation project.
Wordlist originally shared by 'Stun', Anonymous Hacktivist. You can also download it from Torrent.
BeEF 0.4.3.8 - Browser Exploitation Framework
The Browser Exploitation Framework (BeEF) is a powerful professional security tool. It is a penetration testing tool that focuses on the web browser. BeEF is pioneering techniques that provide the experienced penetration tester with practical client side attack vectors.
Unlike other security frameworks, BeEF focuses on leveraging browser vulnerabilities to assess the security posture of a target. This project is developed solely for lawful research and penetration testing.
BeEF hooks one or more web browsers as beachheads for the launching of directed command modules. Each browser is likely to be within a different security context, and each context may provide a set of unique attack vectors.
Joomscan updated - now can identify 673 joomla vulnerabilities
Security Team Web-Center just released an updated for Joomscan Security Scanner. The new database Have 673 joomla vulnerabilities
Joomla! is probably the most widely-used CMS out there due to its flexibility, user friendlinesss, extensibility to name a few.So, watching its vulnerabilities and adding such vulnerabilities as KB to Joomla scanner takes ongoing activity.It will help web developers and web masters to help identify possible security weaknesses on their deployed Joomla! sites.
Check for new updates with command: ./joomscan.pl or check ./joomscan.pl update
The Social-Engineer Toolkit (SET) version 4.7 codename “Headshot” has been released.
The Social-Engineer Toolkit (SET) version 4.7 codename “Headshot” has been released. This version of SET introduces the ability to specify multi-powershell injection which allows you to specify as many ports as you want and SET will automatically inject PowerShell onto the system on all of the reverse ports outbound. What’s nice with this technique is it never touches disk and also uses already white listed processes. So it should never trigger anything like anti-virus or whitelisting/blacklisting tools. In addition to multi-powershell injector, there are a total of 30 new features and a large rewrite of how SET handles passing information within different modules.
Change log for version 4.7
- removed a prompt that would come up when using the powershell injection technique, port.options is now written in prep.py versus a second prompt with information that was already provided
- began an extremely large project of centralizing the SET config file by moving all of the options to the set.options file under src/program_junk
- moved all port.options to the central routine file set.options
- moved all ipaddr.file to the central routine file set.options
- changed spacing on when launching the SET web server
- changed the wording to reflect what operating systems this was tested on versus browsers
- removed an un-needed print option1 within smtp_web that was reflecting a message back to user
- added the updated java bean jmx exploit that was updated in Metasploit
- added ability to specify a username list for the SQL brute forcing, can either specify sa, other usernames, or a filename with usernames in it
- added new feature called multi-powershell-injection – configurable in the set config options, allows you to use powershell to do multiple injection points and ports. Useful in egress situations where you don’t know which port will be allowed outbound.
- enabled multi-pyinjection through java applet attack vector, it is configured through set config
- removed check for static powershell commands, will load regardless – if not installed user will not know regardless – better if path variables aren’t the same
- fixed a bug that would cause linux and osx payloads to be selected even when disabled
- fixed a bug that would cause the meta_config file to be empty if selecting powershell injection
- added automatic check for Kali Linux to detect the default moved Metasploit path
- removed a tail comma from the new multi injector which was causing it to error out
- added new core routine check_ports(filename, ports) which will do a compare to see if a file already contains a metasploit LPORT (removes duplicates)
- added new check to remove duplicates into multi powershell injection
- made the new powershell injection technique compliant with the multi pyinjector – both payloads work together now
- added encrypted and obfsucated jar files to SET, will automatically push new repos to git everyday.
- rewrote the java jar file to handle multiple powershell alphanumeric shellcode points injected into applet.
- added signed and unsigned jar files to the java applet attack vector
- removed create_payload.py from saving files in src/html and instead in the proper folders src/program_junk
- fixed a payload duplication issue in create_payload.py, will now check to see if port is there
- removed a pefile check unless backdoored executable is in use
- turned digital signature stealing from a pefile to off in the set_config file
- converted all src/html/msf.exe to src/program_junk/ and fixed an issue where the applet would not load properly
It can also be downloaded through github using the following command:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
10 Cat Command Examples to Manage Files in Linux / UNIX
Cat command is one of the basic commands that you learned when you started in the Unix / Linux world.
You already know that cat displays a file content. What more could this command do?
This tutorial gives 10 practical usage examples for cat command. Probably few of these examples could be new to you. Or, it might just be a refresher for you, if you already knew these examples.
1. Display the contents of a file
When you pass the filename as an argument to cat, it displays the contents of the file as shown below.
$ cat program.pl
#!/usr/bin/perl
if( 2 ge 3) {
print "greater\n";
}else {
print "lesser\n";
}
You can also display contents of more than one file as shown below.
$ cat program.pl program2.pl
#!/usr/bin/perl
if( 2 ge 3) {
print "greater\n";
}else {
print "lesser\n";
}
#!/usr/bin/perl
@arr = qw(1 2 3);
$ref = \@arr;
print ref $ref;
2. Create a New File
Using cat command, the lines received from stdin can be redirected to a new file using redirection symbols.
When you type simply cat command without any arguments, it just receives the stdin content and displays it in the stdout. So after typed the line once, when you press enter, the same line gets printed in the subsequent line as seen below.
$ cat cat command for file oriented operations. cat command for file oriented operations. cp command for copy files or directories. cp command for copy files or directories.
You can also redirect the stdout to a new file as shown below.
$ cat >cmd_usage.txt cat command for file oriented operations. cp command for copy files or directories. $ cat cmd_usage.txt cat command for file oriented operations. cp command for copy files or directories.
Sometimes you may have to append the content to a file, use >> redirection symbol as shown below.
$ cat >>cmd_usage.txt ls command to list out file and directory with its attributes. $ cat cmd_usage.txt cat command for file oriented operations. cp command for copy files or directories. ls command to list out file and directory with its attributes.
3. Copy File Content
Redirection symbols in unix plays an important role in processing the standard file descriptor contents. Using it, you can copy the contents of one file into another as shown below.
$ cat program.pl >backup_prgm.pl
As seen above, since we used the output redirection, the content displayed in standard output gets directed into a new file called backup_pgrm.pl. View the contents of backup_pgrm.pl:
$ cat backup_pgrm.pl
#!/usr/bin/perl
if( 2 ge 3) {
print "greater\n";
}else {
print "lesser\n";
}
4. Concatenate Contents of Multiple Files
Through cat command, you will be able to concatenate contents of more than one file into a new file.
For example, the codes from program.pl and program2.pl gets combined into a new file all_pgrm.pl.
$ cat program.pl program2.pl >all_pgrm.pl
As seen above, stdout gets redirected and the new file has been created with the contents of program.pl and program2.pl. Verify the contents of all_pgrm.pl:
$ cat all_pgrm.pl
#!/usr/bin/perl
if( 2 ge 3) {
print "greater\n";
}else {
print "lesser\n";
}
#!/usr/bin/perl
@arr = qw(1 2 3);
$ref = \@arr;
print ref $ref;
5. Display Line numbers
To display the contents of a file with the line number in front of each line, use option -n. The following example, prints the line number for the lines from program.pl,
$ cat -n program.pl
1 #!/usr/bin/perl
2
3
4 if( 2 ge 3) {
5 print "greater\n";
6 } else {
7 print "lesser\n";
8 }
9
10
As you noticed above, even the empty lines are numbered. In case of numbering only nonempty lines, use option -b as follows,
$ cat -b program.pl
1 #!/usr/bin/perl
2
3 if( 2 ge 3) {
4 print "greater\n";
5 } else {
6 print "lesser\n";
7 }
Note that the lines which contains whitespaces are not considered as empty lines and the same applicable to line numbered 2.
6. Concatenate File Contents along with Input from Stdin
There is a possibility to read lines from stdin along with concatenation of other files. Hence the user can type his own content whenever its required.
In the following example, you can insert a few lines (from stdin) in the beginning while combining files together.
$ cat - program.pl program2.pl >all_pgrm.pl Contents from file : program.pl, program2.pl
As seen above, – is the place where you can read from stdin, accordingly 1 line from stdin has been inserted into the beginning of a new file called all_pgrm.pl with the latter contents from program.pl and program2.pl files:
$ cat -n all_pgrm.pl
1 Contents from file : program.pl, program2.pl
2 #!/usr/bin/perl
3
4
5 if( 2 ge 3) {
6 print "greater\n";
7 } else {
8 print "lesser\n";
9 }
10
11
12 #!/usr/bin/perl
13
14 @arr = qw(1 2 3);
15 $ref = \@arr;
16 print ref $ref;
7. Don’t Display Repeated Empty Output Lines
Sometimes the file would contain repeated empty lines which you don’t want to display in the stdout while listing it out. cat command provides an option called -s which will suppress consecutive empty output lines into one and displays.
As noticed in the first example of usage 5 (i.e: Display with line number infront of each lines), there is two consecutive empty output lines in the file program.pl numbered 9 and 10. May be you don’t want to display those repeated empty output lines. This can be suppressed as shown below:
# cat -sn program.pl
1 #!/usr/bin/perl
2
3
4 if( 2 ge 3) {
5 print "greater\n";
6 } else {
7 print "lesser\n";
8 }
9
Respectively the line 9 and 10 gets suppressed into one empty line in the above output (i.e:line 9).
8. Display End of Line and TAB characters
You can make the cat to display the $ character at end of every line. Normally by listing file contents, users cant identify whitespaces at the end of each lines, by using the cat -e option.
For instance, use -e option on the file program.pl. As shown below, the third line of this file (i.e:program.pl) is actually not an empty line and as well the line 7 is ending with whitespaces respectively.
$ cat -ne program.pl
1 #!/usr/bin/perl$
2 $
3 $
4 if( 2 ge 3) {$
5 print "greater\n";$
6 } else {$
7 print "lesser\n"; $
8 }$
9 $
10 $
Use option -T to display the tab characters. It displays ^I for TAB character. As shown below, line5 and line7 starts with a TAB character.
$ cat -neT program.pl
1 #!/usr/bin/perl$
2 $
3 $
4 if( 2 ge 3) {$
5 ^Iprint "greater\n";$
6 } else {$
7 ^Iprint "lesser\n"; $
8 }$
9 $
10 $
9. Read Content until a Specific Pattern
The here document can be used along with cat command. For example, when you are reading from stdin, you can read until a line that contains a specific pattern. In the example below, the block of lines are read from stdin (until EOF) and printed on the standard output.
$ cat <<EOF > mv command to move files and directories > top command to display linux tasks > EOF mv command to move files and directories top command to display linux tasks
10. Display File Content in Reverse
This example is a cheater. This is really not a cat command example, but it is related.
tac is the reverse of cat. As you can imagine, tac will just display the contents of a file in reverse order (lines from bottom is displayed first). If you just want to reverse the characters in the line, you should use rev command.
For example, the file program.pl is being displayed in reverse as:
$ tac program.pl
}
print "lesser\n";
} else {
print "greater\n";
if( 2 ge 3) {
#!/usr/bin/perl
Thanx all :)
How to Install RabbitMQ Server and Erlang on Linux
RabbitMQ is an open source message queue server that you can use to build your messaging applications. In simple terms, you can put a message to the queue from one application, and retrieve the message from the queue from the same application, or from a different application. You can use wide varieties of programming languages to connect to RabbitMQ, create and retrieve the messages.
Install Erlang
For RabbitMQ to work, you need to have Erlang installed on your system.
The current stable version of Erlang is R16B, which can be downloaded from Erlang website.
cd /usr/save wget http://www.erlang.org/download/otp_src_R16B.tar.gz tar xvfz /usr/save/otp_src_R16B.tar.gz
After downloading Erlang, install Erlang R16B version from source as shown below.
cd otp_src_R16B LANG=C; export LANG ./configure make make install
Verify Erlang
Now, when you type erl from the command line, you should get the Erlang Shell as shown below. This indicates that you’ve installed Erlang successfully.
# erl
Erlang R16B (erts-5.10.1) [source] [smp:4:4] [async-threads:10] [hipe] [kernel-poll:false]
Eshell V5.10.1 (abort with ^G)
1>
BREAK: (a)bort (c)ontinue (p)roc info (i)nfo (l)oaded
(v)ersion (k)ill (D)b-tables (d)istribution
a
Download RabbitMQ
The current stable version of RabbitMQ server is 3.0.4. When you go to RabbitMQ website, you’ll see the following versions are available for download for Linux platform: 1) Debian / Ubuntu 2) Fedora / RHEL 3) Generic Unix 4) Solaris
In this example, I’ve chosen RabbitMQ for Generic Unix.
cd /usr/save wget http://www.rabbitmq.com/releases/rabbitmq-server/v3.0.4/rabbitmq-server-generic-unix-3.0.4.tar.gz tar xvfz rabbitmq-server-generic-unix-3.0.4.tar.gz cd rabbitmq_server-3.0.4
Start RabbitMQ Server
Start the RabbitMQ server by passing -detached option as shown below.
# cd /usr/save/rabbitmq_server-3.0.4 # sbin/rabbitmq-server -detached Warning: PID file not written; -detached was passed.
If you are getting could_not_start_tcp_listener error message, while starting the RabbitMQ server, see the troubleshooting section below for solution on how to fix this issue.
Verify RabbitMQ Status
Use the rabbitmqctl command to verify the status of the RabbitMQ server and to stop it if required.
# sbin/rabbitmqctl status
Status of node 'rabbit@db-dev' ...
[{pid,30069},
{running_applications,[{rabbit,"RabbitMQ","3.0.4"},
{mnesia,"MNESIA CXC 138 12","4.8"},
{os_mon,"CPO CXC 138 46","2.2.11"},
{sasl,"SASL CXC 138 11","2.3.1"},
{stdlib,"ERTS CXC 138 10","1.19.1"},
{kernel,"ERTS CXC 138 10","2.16.1"}]},
{os,{unix,linux}},
{erlang_version,"Erlang R16B (erts-5.10.1) [source] [smp:4:4] [async-threads:30] [hipe] [kernel-poll:true]\n"},
{memory,[{total,15087368},
{connection_procs,1432},
{queue_procs,2864},
{plugins,0},
{other_proc,4748681},
{mnesia,30672},
{mgmt_db,0},
{msg_index,8652},
{other_ets,369668},
{binary,5976},
{code,6973062},
{atom,387397},
{other_system,2558964}]},
{vm_memory_high_watermark,0.4},
{vm_memory_limit,1699810508},
{disk_free_limit,1000000000},
{disk_free,913096704},
{file_descriptors,[{total_limit,924},
{total_used,3},
{sockets_limit,829},
{sockets_used,1}]},
{processes,[{limit,1048576},{used,124}]},
{run_queue,0},
{uptime,6}]
...done.
To stop a RabbitMQ Server, use the rabbitmqctl command as shown below.
# sbin/rabbitmqctl stop
Troubleshooting
Issue: On CentOS 6, if you’ve used yum to install rabbitmq, or from source as explained above, and if you are getting “BOOT FAILED {could_not_start_tcp_listener,{“::”,5672}}” message, you might have port conflict issue.
Solution: Matahari package that is installed by default on CentOS 6, also runs on port 5672. This process is started by default. Try stopping the qpidd (Qpid AMQP daemon), and see if it solves the problem. If you don’t need Matahari, you can also uninstall matahari, matahari-broker, qpid-cpp-server-ssl and qpid-cpp-server packages.
Stop the qpidd daemon, and disable it from system startup using chkconfig command.
# chkconfig --list | grep -i qpid qpidd 0:off 1:off 2:on 3:on 4:on 5:on 6:off # service qpidd stop Stopping Qpid AMQP daemon: [ OK ] # chkconfig qpidd off # chkconfig --list | grep -i qpid qpidd 0:off 1:off 2:off 3:off 4:off 5:off 6:off
Now, if you start the RabbitMQ server, it should work.
[Troubleshoot] Erratic Mouse Behavior And Error Sound In Windows
On our question and answer section, one of our readers recently reported a very strange problem with his Windows PC. The problem in his words is as below:
My Desktop brings up an error sound but not a code. When I’m working on a program or when I’m on word for example, it works in the program, I’m typing and clicking and typing for a while then suddenly it just like goes out of the program but doesn’t minimize it. I can still see the program open before me but can’t work on it unless I click on it with a mouse. I hear the error code and need to click anywhere on the screen or the program bar to continue what I was busy with. I had made a search for troubles or errors on the computer, I even let my anti-virus scan it but it says all is in order. I have tied to switch USB ports at the back of my computer and I have tried a different mouse and keyboard. Yet I’m still not sure what is wrong… do you know? Can you help me fix it?
Let us try to find out some possible reasons behind it and try to fix the issue.
Suggested Solution
This is a very typical and hard to diagnose problem, but in our experience with Windows PC, the error sound without a code is a typical scenario when a USB device is unplugged. Since you are not unplugging any device, it maybe some fault with the hardware which maybe causing some mounting and un-mounting of USB devices. To verify if the sound is because of a hardware change notification, which is usually without an error code, open Device manager by running devmgmt.msc on the run prompt or command prompt.
On Device Manager window, keep a close eye on the USB section when you hear the sound again and see if there is any change.
We also suggest to do a complete virus scan of the PC to ensure that this error sound and activity is not triggered because of some malicious script or software or a virus infection on your computer.
Transfer your Domain to blogger ( Domain point to bogger)/ Edit Your DNS
How to Edit DNS Record when function is not provided with domain controller like crazydomains.in
Hello Friends,
Today one of my friends ask this problem then i am making this tut.
For transferring your domain to your blog on blogger.com Just go to basic setting write your top leve domain name and you will be provided two CNAME settings to be edited on the DNS of name server of domain.
It is easy to update the CNAME in domain DNS setting but when you purchase your domain at lower price some domain controller does not provide you to edit DNS setting you can update only nameservers.
So how will you do it.
Here is tut for this,
1. Go to your domain controller and update name server there
ns1: ghs.google.com
( IT does not matter you can put watever else.)
2. Now do the same thing as told above. Go to basic settings tab and update your domain you will get two
CNAME there like this
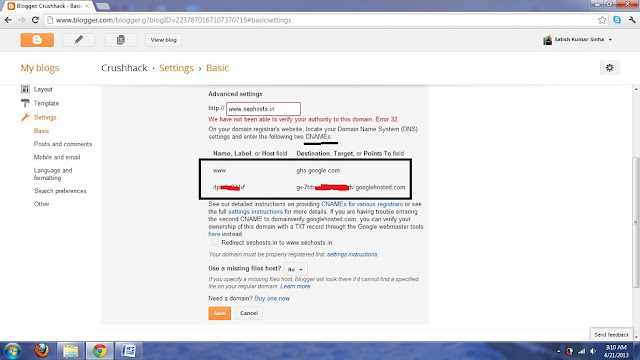
3. Step: Now Use Cloudflare.com for editing you DNS :)
Create an Account on Cloudflare its Free.
provide the domain name it vl take 40 sec to detect all you DNS Settings.
When it shows you all the DNS just Delete all DNS settings watever is there.
Then add two CNAME as per given in blogger.com
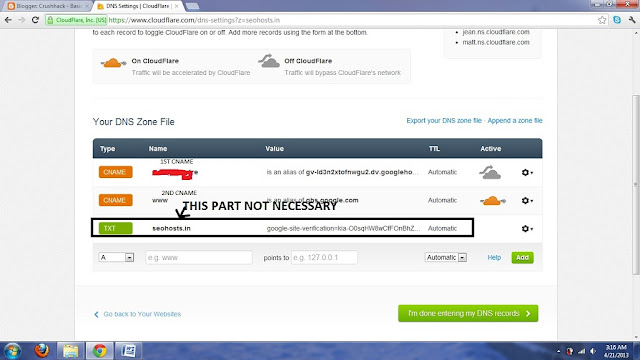
Now Cloudflare will provide you two nameservers
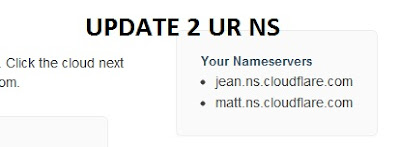
Now update these nameserver provided in your Domain Control.
Wait for 2- 3 hrs for updation of DNS records. when done,
4. Just go to your Blogger Setting and update your domain name and its done.
**Note Choose all Setup free in Cloudflare :)


.jpg)

.jpg)










.jpg)









.jpg)




