- More than 30 modules to automatize administration and post exploitation tasks:
- Execute commands and browse remote filesystem, even with PHP security restriction
- Audit common server misconfigurations
- Run SQL console pivoting on target machine
- Proxy your HTTP traffic through target
- Mount target filesystem to local mount point
- Simple file transfer from and to target
- Spawn reverse and direct TCP shells
- Bruteforce SQL accounts through target system
- Run port scans from target machine
- And so on..
- Backdoor communications are hidden in HTTP Cookies
- Communications are obfuscated to bypass NIDS signature detection
- Backdoor polymorphic PHP code is obfuscated to avoid HIDS AV detection
Showing posts with label Hacking. Show all posts
Showing posts with label Hacking. Show all posts
Saturday, April 20, 2013
Weevely : Stealth PHP web shell with telnet style console
Nessus 5.0.2 vulnerability scanner updates
Nessus is the world’s most widely-deployed vulnerability and configuration assessment product updated to version 5.0.2 .Nessus 5 features high-speed discovery, configuration auditing, asset profiling, sensitive data discovery, patch management integration, and vulnerability analysis of your security posture with features that enhance usability, effectiveness, efficiency, and communication with all parts of your organization.
Nessus 5.0.2 change logs:
- UTF8 encoding problems would sometimes cause the generation of reports to fail
- Fixed a case where generating some compliance checks reports would cause the scanner to hang, using 100% of the CPU
- Resolved a resource leak issue occurring when a large number of different users are connected at the same time .
- Network congestion errors are now detected more conservatively
- Upgraded libxml2, libxslt, openssl to their newest versions
- Some nessusd.rules directives were not honored by the port scanners
- Solaris 10 build
BeEF 0.4.3.8 - Browser Exploitation Framework
The Browser Exploitation Framework (BeEF) is a powerful professional security tool. It is a penetration testing tool that focuses on the web browser. BeEF is pioneering techniques that provide the experienced penetration tester with practical client side attack vectors.
Unlike other security frameworks, BeEF focuses on leveraging browser vulnerabilities to assess the security posture of a target. This project is developed solely for lawful research and penetration testing.
BeEF hooks one or more web browsers as beachheads for the launching of directed command modules. Each browser is likely to be within a different security context, and each context may provide a set of unique attack vectors.
Transfer your Domain to blogger ( Domain point to bogger)/ Edit Your DNS
How to Edit DNS Record when function is not provided with domain controller like crazydomains.in
Hello Friends,
Today one of my friends ask this problem then i am making this tut.
For transferring your domain to your blog on blogger.com Just go to basic setting write your top leve domain name and you will be provided two CNAME settings to be edited on the DNS of name server of domain.
It is easy to update the CNAME in domain DNS setting but when you purchase your domain at lower price some domain controller does not provide you to edit DNS setting you can update only nameservers.
So how will you do it.
Here is tut for this,
1. Go to your domain controller and update name server there
ns1: ghs.google.com
( IT does not matter you can put watever else.)
2. Now do the same thing as told above. Go to basic settings tab and update your domain you will get two
CNAME there like this
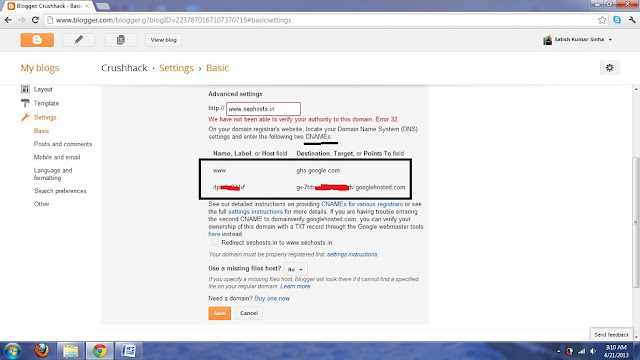
3. Step: Now Use Cloudflare.com for editing you DNS :)
Create an Account on Cloudflare its Free.
provide the domain name it vl take 40 sec to detect all you DNS Settings.
When it shows you all the DNS just Delete all DNS settings watever is there.
Then add two CNAME as per given in blogger.com
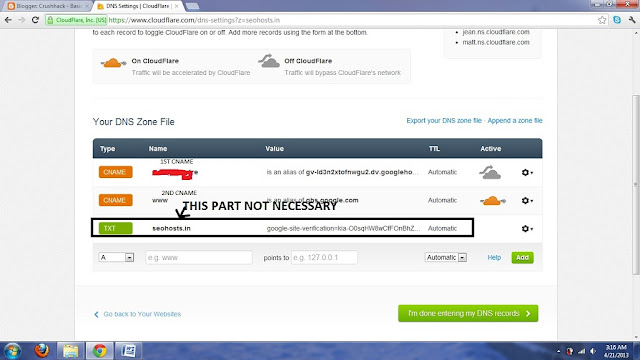
Now Cloudflare will provide you two nameservers
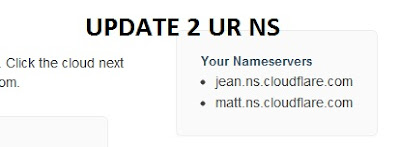
Now update these nameserver provided in your Domain Control.
Wait for 2- 3 hrs for updation of DNS records. when done,
4. Just go to your Blogger Setting and update your domain name and its done.
**Note Choose all Setup free in Cloudflare :)
Monday, September 17, 2012
WEP Cracker Using fern wifi cracker
A very good tutorial by my friend harpreet singh on Wep Cracking. He has used the tool "fern-wifi-cracker" which is easily avaliable on backtrack 5 R3.
So lets begin ...
Go to backtrack --> exploitation tools --> wireless exploitation tools -->
WLAN exploitation --> fern-wifi-cracker
Now select the wireless interface you have ( it can be wlan0, wlan1 etc..)
Now there's a button on which you can see wifi logo, click that and it will start the network scanning ( of-course its using airodump here).
Note*: if you double-click anywhere in the tool, you'll get a "settings" dialog box... you can set the channel there and also you can start the xterm.
Note*: if you double-click anywhere in the tool, you'll get a "settings" dialog box... you can set the channel there and also you can start the xterm.
Now if you see closely, you'll note that the two buttons below the scan button will get enabled, the first button is the WEP cracking button and the second one is for WPA cracking.
Click the button for WEP cracking
Click the button for WEP cracking
After clicking that button, a new dialog box will open. you can select the wep network from the list and then you can select the type of attack i.e arp replay attack, chop-chop attack or fragmentation attack. then click "Attack"...
You'll be able to see the number of ivs are increasing.There's a progress bar at the end of the dialog box.When the progress bar reaches the end, this tool starts aircrack for cracking wifi password
When the password is cracked, it will be shown at the bottom of the dialog box...
NOW COMES THE INTERESTING PART:
(before going further, i suggest you to connect to the internet for this)
Go to "toolbox" --> Geolocatory tracker.
NOW COMES THE INTERESTING PART:
(before going further, i suggest you to connect to the internet for this)
Go to "toolbox" --> Geolocatory tracker.
Give the bssid of the AP in the text box and click "Trace".
I think everyone has already guessed what it will show...
YES... INDEED... IT WILL SHOW YOU THE LOCATION OF THE AP ON THE GOOGLE MAPS ... You can see the coordinates as well..
YES... INDEED... IT WILL SHOW YOU THE LOCATION OF THE AP ON THE GOOGLE MAPS ... You can see the coordinates as well..
And also you can see in the toolbox, there's a button for cookie hijacking called "cookie hijacker" ..
ok guys so that's it for now... :-)
ok guys so that's it for now... :-)


.jpg)

.jpg)



















.jpg)
.jpg)


